A poorly optimized user journey is like telling your customers to flee and never come back.
Users are constantly asked to provide passwords, identifiers, security codes, facial recognition, etc.
Adding even more frustration can be fatal for your business.
We know that fintechs need to maintain a sufficient degree of security to prevent customers from being impersonated, while keeping the user journey smooth and frictionless.
This is no small feat, because if certain steps in the login process encounter bugs and drag on, users will feel frustrated and may give up along the way, or even never use the service again.
It's a big challenge: How do you make a fintech both safe and simple? This requires real teamwork, especially on the part of the Product Manager, who has the difficult task of harmonizing teamwork to develop a product that meets the needs of users.
What are the security requirements in fintechs?
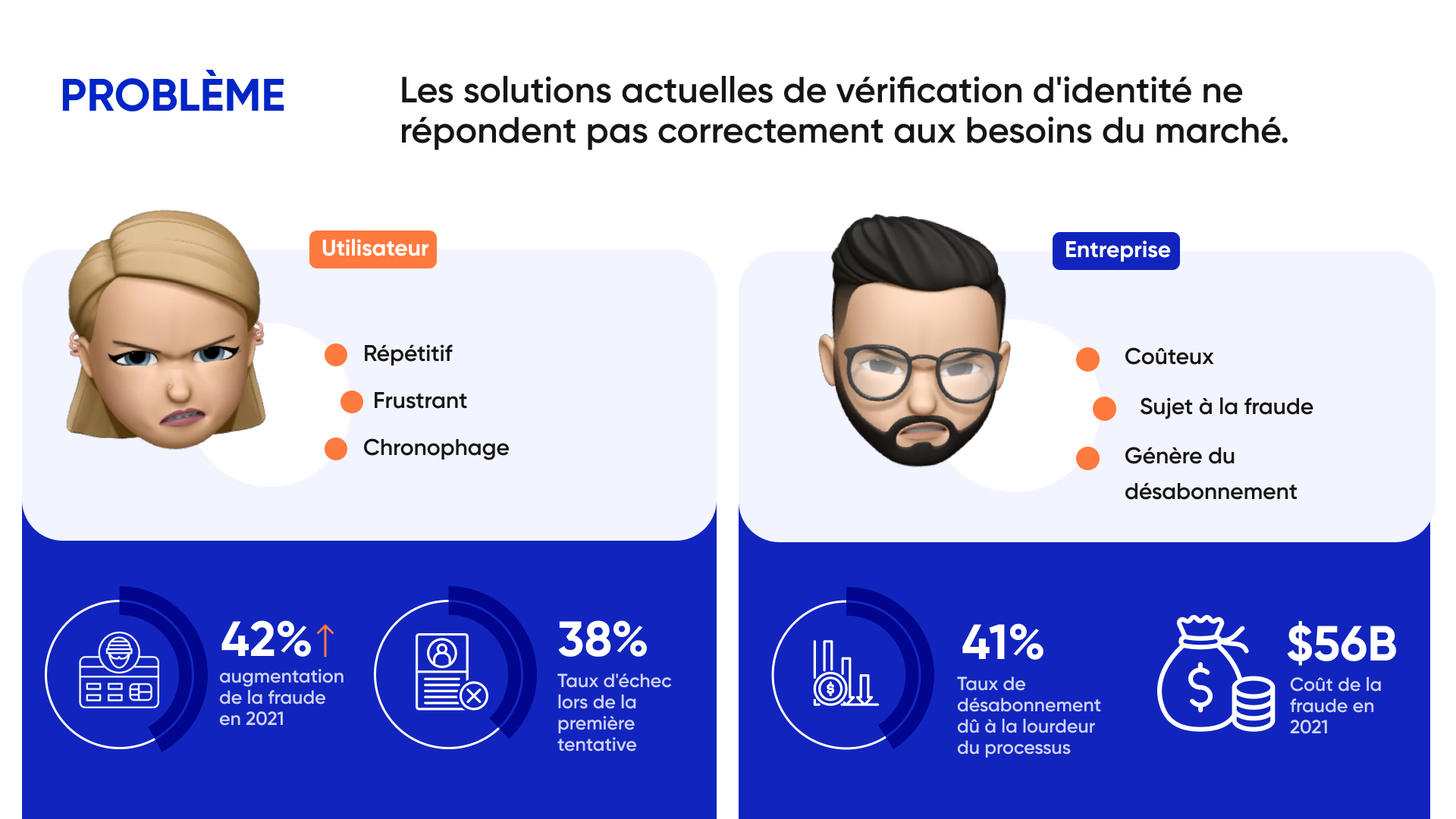
The user, in order to connect to his account, must go through several steps to confirm that he is who he says he is.
These identity verification steps are becoming more and more stringent as fraudsters are becoming smarter. It can be tempting to simplify procedures as much as possible to make the service less frustrating, while neglecting safety.
This is a risky bet, as a simple code will not be enough to discourage fraudsters and exposes the customer, as well as the integrity of their funds, to a major risk.
User experience challenges in fintechs
- Authentication is becoming more and more stringent: methods like two-factor authentication (2FA) or multi-factor authentication (MFA), while effective in increasing security, introduce additional steps into the login process, generating friction for the user.
- Failed authentication attempts: they require the user to repeat the same steps, often because the technology is not efficient enough.
- The mix of authentication methods can confuse the user: The diversity of options (SMS, email, authentication applications, authentication applications, physical security keys, biometric recognition) can confuse those less comfortable with technology.
- Accounts blocked in case of an authentication error: If the authentication is inaccurate, it can also lead to errors and prevent a user from accessing their accounts. This can lead to disastrous business consequences, such as negative reviews, bad advertising, unsubscriptions, and complaints.
How can the Product Manager improve the user experience in a fintech?
- Use advanced technologies : the use of new technologies, such as artificial intelligence or biometric recognition behavioral, can help you create more fluid and non-intrusive authentication methods.
- Focus on the speed and fluidity of the journey : users want interactions that are fast and uninterrupted. Bugs or slow loading can lead to user frustration or even disengagement. Choose authentication technologies that process quickly.
- Make your solution simple and fun : Authentication processes should be intuitive and easy to understand, even for novice users. Do not hesitate to guide the user through each step, or even add definitions that specify the purpose.
- Avoid failed attempts as much as possible : authentication must be reliable and work with the minimum number of flaws. Technical issues can not only cause frustration but can also reduce trust in the tool. To do this, choose authentication solutions that are recognized for their high success rate.
- Be transparent every step of the way : clearly explain to users why certain personal information is requested and how they will be used and stored.
- Personalize identification: offering options for users to choose their preferred authentication method can improve the overall experience. The ideal would be a customizable solution with several possible authentication methods adapted to each use case.
- Deliver immediate returns : clear and immediate feedback must be provided during the authentication process to guide and reassure the user, especially in case of failure.
Examples:

Our solution was designed to provide an optimal user experience for fintech users. AI-guided onboarding and reauthentication with a simple smile.
Accompanied by the best experts in document fraud from the Gendarmerie Nationale, ShareID provides a strong and compliant authentication solution that allows secure identity verification.
Our particularity is our method of managing and securing the personal and biometric data of our users. In fact, we never store data and thus avoid any risk of theft or possible alteration of your personal data.
Contact us today to find out more about our strong authentication solutions.






.png)